Email Security and Authentication
Think Like an Email Expert: How to Troubleshoot DKIM Alignment Failures
minute read

Cyberattacks are on the rise worldwide—and these attacks are getting more sophisticated by the day. Since over 90 percent of cyberattacks start with email, keeping your email program secure has never been more important.
This starts with email authentication.
Email authentication is a sender’s best defense against phishing and spoofing attacks.
But it isn’t foolproof. Ultimately, mailbox providers (MBPs) like Gmail, Yahoo, and Microsoft have the final say in which emails get delivered and which don’t. Sometimes, legitimate email senders suffer based on these decisions—and are left wondering why their authentication failed and what to do about it.
To illustrate this point, let’s explore why a Validity client saw failure reports with DKIM (DomainKeys Identified Mail) and how they fixed the problem.
Why is email authentication important?
First, let’s back up a little.
Why is email authentication so important? Because it empowers MBPs to confirm and verify the identity of an email sender.
We like to compare email authentication to a passport. You absolutely need a passport when traveling to let people know who you are. Do you think you’d be authorized to travel across the world with no proof of your identity? You could try, but we guarantee it won’t work!
Authentication protocols, including SPF, DKIM, and more recently, DMARC, protect your domain, IP, and most importantly, your subscribers, from spoofing or phishing attacks.
The problem: DKIM alignment failures
Ready to get technical? Next, let’s look at how authentication failures impacted one specific email program.
Like SPF, DKIM is a critical protocol to DMARC (Domain-based Message Authentication Reporting and Conformance). When DKIM alignment fails—or when the d= value in the Header From does not match the d= value in the DKIM signature—it can negatively impact deliverability, as mailbox providers may send the message to the spam folder or block it entirely. (Get a refresher of how DKIM works here.)
Recently, DKIM alignment results for one of our clients’ legitimate sending domains were failing approximately 30 percent of the time, while the DKIM signature itself passed at a rate of more than 99 percent.
The client couldn’t understand why DKIM alignment wasn’t consistently successful when all emails were signed in the same way.
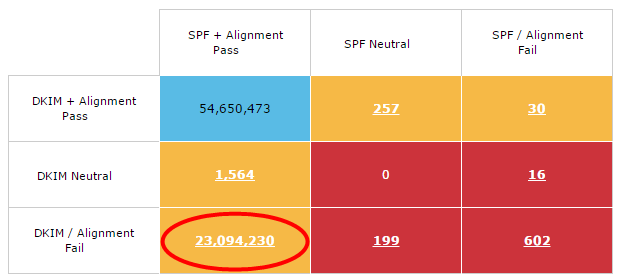
The chart below shows a matrix of the client’s email authentication failures over a one-week period.
The culprit: Multiple DKIM signatures
To send emails from the domain in question, our client used a third-party email service provider (ESP).
Upon investigation, we saw that their emails were signed with two DKIM signatures, as is permitted by the spec. The first signature had a d= value matching the ‘Header From’ domain of the email, and the second had a d= value pertaining to a domain belonging to the third-party sender.
As a reminder, for a message to pass DKIM alignment, the d= value in the DKIM signature must match the d= value in the ‘Header From’ address.
By drilling down into the result reported by each MBP, we saw that the MBPs reporting both DKIM pass and DKIM alignment were using the d= value in the first signature—which matched the d= domain in the ‘Header From’—to check alignment. Because of this match, the mailbox providers reported a positive result.
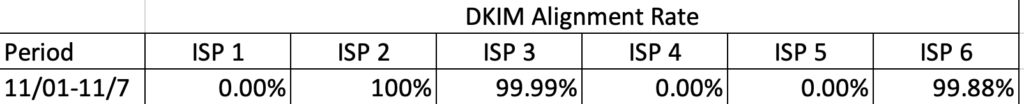
However, there were three mailbox providers that reported an alignment failure. The culprit in these cases was the d= value in the second signature, as it didn’t match the ‘Header From’ address.
The chart below shows the seven-day alignment pass rate per ISP during the failure period.
The solution: Remove the second DKIM signature
After discussing the issue with their ESP, the client determined that the second DKIM signature was superfluous and could be removed from the signing process entirely.
Once the client made this change, there was a brief (and expected) period when the mailbox providers provided varying results.
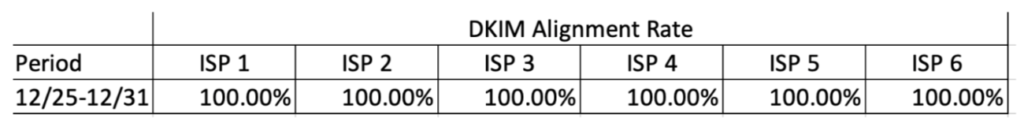
But eventually, all mailbox providers eventually began to report a more than 99 percent pass rate for both the DKIM checks and alignment.
The chart below shows the seven-day alignment pass rate per ISP after the failure period.
The lesson: Communication is key
While diagnosis is a critical first step to troubleshooting an email authentication problem, an equally critical component is communication—both internally between your marketing and security departments, and externally between your third-party ESPs, mailbox providers, and email authentication partner(s).
Due to the level of collaboration needed to resolve authentication issues, it’s essential to set a standard process to follow when these problems arise.
This will ensure that your team knows how to identify an authentication issue and what details to know or provide to solve it.
As you can imagine, clearly defining where and what the problem is a great first step to finding a solution.
The email marketer’s role
To correctly identify and diagnose authentication issues, regular monitoring of your program’s infrastructure is a must.
While email marketers don’t need to master every aspect of DKIM, they should be able to spot when things go wrong.
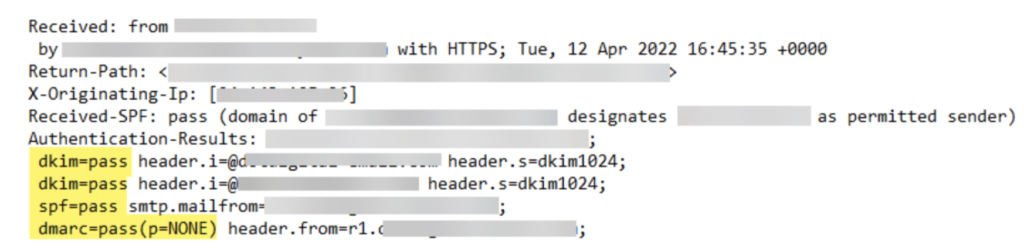
To do so, regularly check your authentication parameters in email headers.
As you can see below, it’s easy to see if the different criteria are compliant (‘i.e., equal to PASS’) or if there are issues.
Working with key stakeholders
To prevent DKIM alignment issues before they arise, marketers need to work collaboratively with several key stakeholders.
At some organizations, ESPs are responsible for email authentication. If this is the case at your company, make it a point to communicate regularly with your email service provider and verify that the DKIM protocol is set up correctly.
For other senders, email authentication is handled by internal IT or security teams. So, you’ll need to work closely with these individuals to ensure everything is compliant.
Let’s say you’ve verified your authentication parameters, but the issue persists. In that case, there might be an issue on the mailbox provider’s side: They may not recognize your domain/IP as they should.
Regardless of the specific DKIM issue, maintaining positive, transparent relationships with these stakeholders will help your email program run optimally.
Conclusion
Email authentication protocols like DKIM are essential to maintain your email deliverability, or your ability to reach subscribers’ inboxes.
To learn other factors that can make or break your email deliverability, read “The 5 Minute Guide to Email Deliverability.”