I’ve come across several clients recently that are not aware of how a feedback loop works and how it can be used. I’m hoping this blog will be a useful reference point for those types of conversations.
What is it?
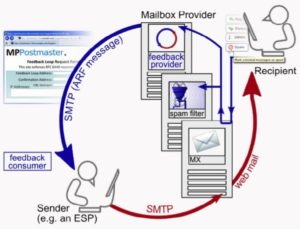
When a recipient has decided to click “This is Spam” on your email, it is considered a “complaint.” Some mailbox providers allow visibility for when this happens by allowing the sender to sign up for a feedback loop. Feedback loops, or FBLs, allow senders to receive messages back from members who complained. The mailbox provider forwards the message complained about back to the sender at a designated email address that has been set up, primarily so that the sender can suppress this user in their database. See the diagram below:
What Mailbox Providers use FBLs?
Unfortunately, not all mailbox providers give senders the option for a feedback loop process to be set up. However, there are several providers that have set this up for your benefit. Below you’ll find links for those available so that you can signup:
- Return Path’s Universal Feedback Loop brings all Return Path hosted FBLs into one cohesive and actionable location. The list of providers covered under this tool are below:
Bluetie/Excite
Comcast
Cox
Fastmail
LaPoste.net
Libero (Italiaonline)
Locaweb
Mail.ru
OpenSRS/Hostedmail (Tucows)
Rackspace
Synacor
Telenor
Terra
BAE Systems (USA.net)
XS4ALL
Yandex
- AOL
- Earthlink
- Gmail Complaints are not sent in ARF format and the data is more valuable for high volume senders. Sign up with Gmail Postmaster tools to view feedback loop data
- Outlook.com (Hotmail)
- QQ (Tencent)
- Yahoo!
- Zoho
How do I get it?
The sender must go through an application process to enable a feedback loop with a mailbox provider, and can be found on the sites shown above. The information required will vary across the different applications. Some of the essential items you will be asked to enter include contact information, IP address, and what email address has been set up on your end to receive the messages. Specifically Yahoo!, requires senders to authenticate with DKIM to enable the feedback loop process. In Yahoo!’s application you will be asked for the d= and s= values from your DKIM signature, so have that ready!
What do I need to do?
Feedback loop email address:
You will need to set up an email account on your end that will receive the messages being sent back from the mailbox providers. This email address should have a parsing script looking through all the messages coming in to remove the needed information.
Collect data:
The information being sent back to the sender’s feedback loop email address is simply a copy of the message that the complaining member received. The most popular format that most mailbox providers use is Abuse Reporting Format (ARF). Now, the sender can collect any information it wants from this message it received back, which includes the header and body of the message. At the very minimum, the sender should strip out the email address so that it can be added to the suppressed list. Unfortunately, mailbox providers sometimes redact the member’s email address from the message sent back, so the sender should find another way to identify the member from the message. This can be done through tracking links in the body or subscriber identifiers in the x-header that the sender has put in place.
What are the benefits?
Remove complaining members:
The main purpose for the feedback loop process is to be able to unsubscribe a member from your database. You want to avoid members submitting multiple complaints, which will hurt your deliverability. Aside from that, complaints also drive future emails to a member’s spam folder. As mailbox providers are moving more toward engagement, the amount of mail going into the spam folder can also hurt your reputation.
Identify compromised hosts:
Network security is something not to be taken lightly. FBLs help point out security issues by letting the sender see all complaints for the sender’s IP address space. If your IP addresses have been compromised, you may receive complaints on pieces of mail that you never sent.
Identify problematic campaigns/acquisition methods:
Collect more information from feedback loops like a campaign ID number or list acquisition ID in the header. Take the first step in identifying which campaigns are most problematic, followed up with an evaluation of factors like content and frequency. This is also a great tool if you have multiple list sources. It could be that you have a more problematic list source that needs to be reevaluated or segmented into another IP address, to not harm the rest of your email program.